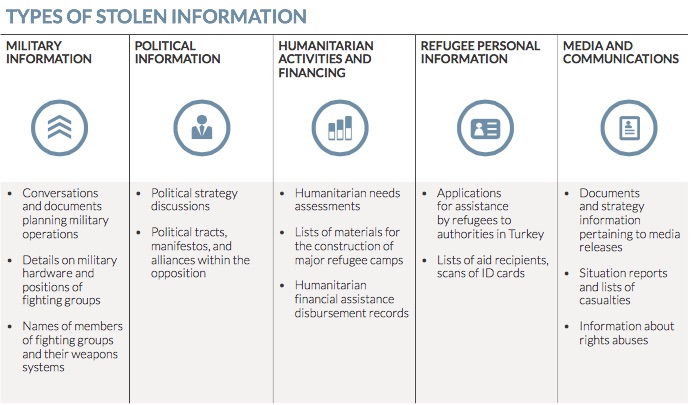
Hackers in Lebanon with alleged ties to Hezbollah and the pro-Assad regime have stolen military information, political information, refugee personal information, and information on humanitarian activities and financing, according to FireEye, a US cyber security company. Data stolen includes over 7 gigabytes of sensitive data, over 31,000 conversations, over 12,000 contacts and nearly a quarter of a million messages. Unlike common cyber threats, this is not just cyber espionage aimed at achieving an information edge or a strategic goal. Rather, this activity, which takes place in the heat of a conflict, provides actionable military intelligence for an immediate battlefield advantage. It provides the type of insight that can thwart a vital supply route, reveal a planned ambush, and identify and track key individuals. This intelligence likely serves a critical role in the adversary’s operational plans and tactical decisions. However, this tactical edge comes with a potentially devastating human cost.
According to FireEye’s February 2015 report, in mid-2013, ten armed units working in opposition to Syrian President Assad’s regime were planning a major operation intended to push a front forward against the Syrian government’s forces. They carefully laid out their objective— take and hold a series of positions and liberate the town of Khirbet Ghazaleh, a strategic gateway to the major city of Daraa. They used Google Earth to map their defensive lines and communicate grid coordinates.
They shared photocopied battle plans and in red ballpoint pen added defensive berms, saving their plans electronically as pictures. They planned for a battle involving between 700 and 800 opposition forces, who were divided into groups to launch separate attacks, including an ambush. They mapped out locations for reserve fighters, staging areas, and support personnel, settled on a field operations area, and planned supply routes to resource their forces. They sternly told commanders of each unit that they could make no ‘individual’ decisions without the approval of the Operations element.
The would begin the attack with a barrage of 120mm mortar fire, followed by an assault against key regime troop locations. They drew up lists of men from each unit, with names, birthdates, and other identifying information. They used formulas in a colorful Excel spreadsheet to calculate per-man ammunition needs. They arranged and assigned heavier weapons to various engagements: several tanks, a BMP fighting vehicle, 14.5mm and 23mm anti-aircraft guns, B-10 82 mm recoilless rifles, Yugoslav 90mm M79 Osa anti-tank weapons and other equipment.
Finally, they prepared and staffed medical teams and battlefield ambulances. They would have a driver, stretcher-bearer, and two armed elements for additional support.
FireEye uncovered these battle plans in the course of their ongoing threat research. They came across stolen documents containing the secret communications and plans of Syrian opposition forces that had fallen victim to a well-executed hacking operation. Between at least November 2013 and January 2014, the hackers stole a cache of critical documents and Skype conversations revealing the Syrian opposition’s strategy, tactical battle plans, supply needs, and troves of personal information and chat sessions belonging to the men fighting against Syrian President Bashar al-Assad’s forces.
Opposition battle plans were stolen that included information about the emplacements of anti- government forces. The stolen plans are high-value artifacts that may have provided actionable military intelligence to the recipients.
Female Attraction
The hackers would pretend to be a seemingly sympathetic and attractive women in conversations with their victims on Skype. As the conversations progressed, the “femme fatale” would offer up a personal photo, laden with malware and developed to infiltrate the target’s system.
When the victim opened the file it would display a picture of a woman, but silently in the background the DarkComet malware was installed, giving the hackers remote access to the victims’ computer.
The hackers managed to weave a question into the Skype conversation prior to sending the malware-laden image to ascertain whether their targets were using a Windows PC or Android smartphone, and tailor the malware accordingly.
In order to avoid being caught out, the hackers created a Facebook profile for their fake female avatar which used the same picture and was filled with pro-opposition rhetoric. The hackers also maintained a fake Syrian opposition website which purported to support the rebels but which in fact hosted the same DarkComet malware.
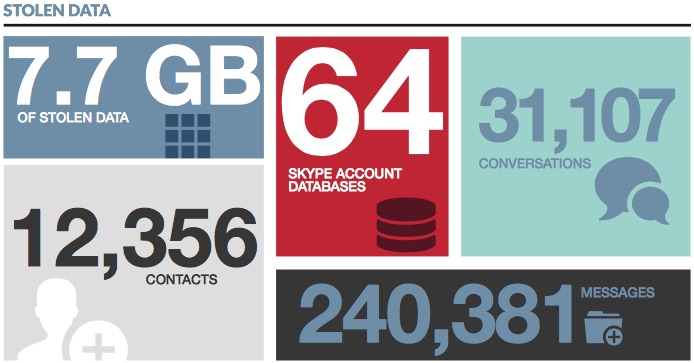
In total the hackers were able to breach the accounts of 64 victims, with most based in Syria or Turkey, stealing 7.7GB of data including 12,356 contacts, 31,107 conversations, and 240,381 messages.
It is unknown if any of the stolen information has been used to actively target opposition fighters or thwart opposition attacks.
Lebanon: A Recurring Theme
FireEye has not specifically named the group of hackers behind the attacks, but multiple references to Lebanon were found during the company’s research:
“While researching this activity, we came across numerous references to Lebanon. We observed a user in Lebanon upload what appear to be two test versions of malware used to target opposition elements (the YABROD downloader and the CABLECAR launcher). The avatars, social media seeding, and fake opposition website are also filled with references to Lebanon. During chats, for example, the female avatars often state that they are in Lebanon and demonstrate familiarity and interest in talking about issues there. Social media pages suggest that the avatars are refugees in the country, or are Lebanese.”
FireEye came upon a reference to a 3-day training course in Lebanon in 2012 that described the use of eerily similar methods. According to media reports, a leaked Syrian intelligence memo titled “Training Course for Internet and Social Media Activists” describes the tactics that pro-Assad recruits—many of whom were Lebanese members of Hezbollah’s Islamic Resistance—were trained to use.
The training included:
- Establishing an “Electronic Army” to infiltrate Syrian activists’ computers, websites and Internet accounts, and attempting to use stolen personal information against them.
- Setting up opposition social media accounts to spread false information and make accusations and counter-accusations
to create conflict between opposition members in and out of Syria. - The use of women to entrap opposition members and activists using social media sites such as Skype and Facebook.
FireEye Report, YL

Leave a Reply
You must be logged in to post a comment.